Basic of Caching
Cache란 Web Server와 User 사이에 위치하여 Web Service간의 통신을 효율적으로 도와준다.

Web Server의 데이터를 이 Cache에 미리 저장해두고, 사용자에게 저장된 데이터를 제공하여 서비스 속도 향상을 토와주는 것을 Caching이라 한다.
Web Server 뿐만 아니라 Browser에도 Cache가 존재한다. 웹 데이터를 빠르게 Load하기 위해 로컬 PC에 이미지, 자바스크립트 등의 데이터를 저장하고 있다. User가 Cache 데이터를 저장해둔 Website에 접근 시, 서버에서 데이터를 불러오는 게 아닌, 로컬 PC에서 데이터를 Load하기 때문에 속도 측면에서 빠르다. (대표적인 Cache를 이용하는 서비스로는 CDN이 있다.)
Explanation about Cache Keys
웹서버의 데이터에 대한 요청을 받을 때마다 Cache는 요청을 서버로 전송해야할 지, 아니면 이미 로컬 PC에 저장된 데이터로 응답할 수 있을 지를 결정해야 한다. 이를 식별하는 값이 Cache Key다. Cache Key는 서버에 요청되는 값 일부를 떼어내서 Request 일부와 상응하는 Response를 저장한다. (Request의 모든 부분을 확인하지 않는다.)
보통 Host, Path를 신뢰한다.
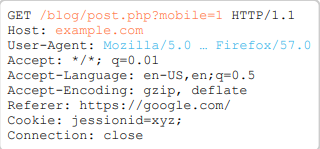
위 Request에서 오렌지 색으로 칠해진 부분이 일반적인 Cache Key다.
What is Cache Poisoning Attack?
문자 그대로 Cache에 악의적인 데이터를 남겨 다른 사용자가 의도하지 않은 동작을 하도록 하는 공격이다.
흐름 간단 요약 :

Case Study :
레퍼런스에 많은 공격 케이스가 있는데, 가장 기본적인 것만 살펴보자. PortSwigger가 Redhat에 보고한 내용이다.

위 요청에서 공격자가 X-Forwarded-Host 헤더가 meta 태그 안에서 URL을 생성되기 위해 사용된 것을 Response에서 확인할 수 있다. 이 헤더를 조작하여 XSS 코드를 삽입하면 Reflected XSS Trigger가 가능해진다.

XSS 코드를 삽입한 데이터가 Cache로 저장된 후, 다른 User들에게 전달되면 User측에서 Reflected XSS가 발생한다.
이외 Case들은 레퍼런스들을 통해 확인하면 된다.
Reference :
https://portswigger.net/kb/papers/7q1e9u9a/web-cache-poisoning.pdf%20